Advanced Threat Analytics–Attack Simulation and Demo–Part1
Advanced Threat Analytics–Attack Simulation and Demo–Part2
Advanced Threat Analytics–Attack Simulation and Demo–Part3
Microsoft Advanced Threat Analytics (ATA) is an user and entity behavior analytics solution to identify and protect protect organizations from advanced targeted attacks (APTs). You can read more information about Microsoft Advanced Threat Analytics (ATA) here. The purpose of this blog is to provide a few methods which can be used to simulate and demonstrate some of the basic attacks for demo and testing purpose.
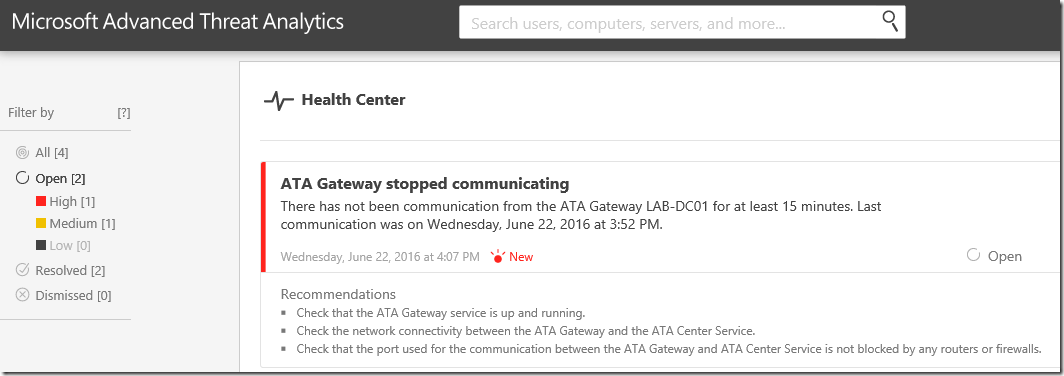
Suspicious Activity Simulation #1 – ATA Gateway Stopped Communicating
We will start with the most obvious one! – ATA communication issue. In this scenario, I am using ATA Light Weight Gateway (LWGW). In this case Microsoft Advanced Threat Analytics Gateway (ATAGateway) service should be running on Domain Controllers.
To simulate this scenario,
- Identify all Domain Controllers from the forest/domain. You can use the following DSQUERY command to get all DCs from the domain.
- DsQuery Server -Forest
-
- Stop the ATAGateway service remotely
- Or we can use a simple SC command – SC \\Lab-DC01 stop ATAGateway
You will receive the following high alert – ATA Gateway Stopped Communicating – in Health Center.
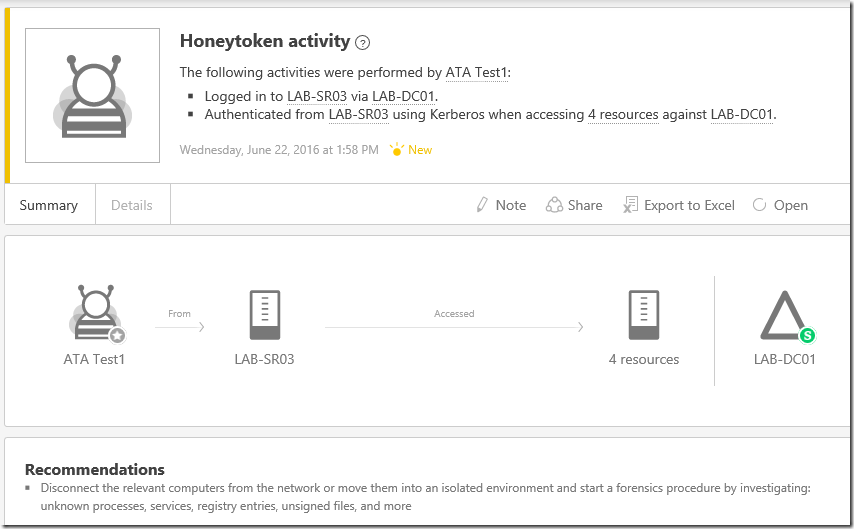
Suspicious Activity Simulation #2- Honey Token Account Activities
In general, the Honey Token accounts are non-interactive accounts. These accounts can be dummy accounts for detect malicious activities.
To simulate this scenario,
- Create two 2 user accounts in Active Directory (ATA-Test1 and ATA-Test2)
- Add ATA-Test2 to Domain Admins group
- Get the SID of ATA-Test1 and ATA-Test2 using PowerShell or DSQUERY command
- Add this SID as Honey token accounts (ATA Console –> Configuration –> Detection –> Honeytoken Account SIDs). Save the configuration.
- Establish an integrative logon session using these accounts. You can RDP into a machine use these accounts
Honey Token accounts (non-sensitive)
You will receive the following alert/email with recommended actions in the ATA console.
Honey Token accounts (Sensitive)
Since ATA-Test2 account is a domain admin account, you will receive the same alert with "Sensitive (S )" indicating that this account is a high privileged account in Active Directory.
Suspicious Activity Simulation #3 – Massive Object Deletion
Bulk object deletion can be a suspicious activity in an Active Directory environment. ATA can alert alert you based on massive object deletion activities.
To simulate this scenario,
- Create a few users in Active directory. Here is a sample PowerShell script which you can use to create test accounts in Active Directory
Clear
Import-module activedirectory
$pass = ConvertTo-SecureString "MyPassword0!" –asplaintext –force
for ($i=0;$i -lt 100;$i++)
{
$accountname = "Test-Account$i"
Write-Host "Creating $accountname" -NoNewline
New-ADUser –SamAccountName $accountname –name $accountname -OtherAttributes @{'description'="ATA Test User Account"} -Path "OU=Test Accounts,OU=User Accounts,DC=labanddemo,DC=com"
Set-ADAccountPassword –identity $accountname –NewPassword $pass
Write-Host "...Done"
}
You will receive the Massive Object Deletion alert in the ATA console right away as shown below.
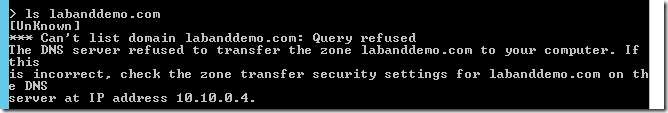
Suspicious Activity Simulation #4 - Reconnaissance using DNS
The DNS or name resolution information in a network would be useful reconnaissance information. In general, DNS data contains a list of all the servers and workstations and the mapping to their IP addresses. Verifying this information may provide attackers with a detailed view of the environment allowing attackers to focus their efforts on the relevant entities.
For this simulation, the plan is to perform a DNS zone lookup using NSLOOKUP LS command.
To simulate this scenario,
- Logon to a remote server.
- Open Command Prompt and run NSLOOKUP command
- From the NSLOOKUP window, run LS command to list the DNS zone
You will receive the following Reconnaissance using DNS alert the ATA console.
Advanced Threat Analytics–Attack Simulation and Demo–Part1
Advanced Threat Analytics–Attack Simulation and Demo–Part2
Advanced Threat Analytics–Attack Simulation and Demo–Part3



















9 comments:
Hi SANTHOSH SIVARAJAN,
Thank for your article. Very useful....
Hope you post part 2 and part 3 as soon as possible
Thanks Huy Pham. Yes. 2nd part is coming soon.
Great article. Any news on part 2?
Thank you
The effectiveness of IEEE Project Domains depends very much on the situation in which they are applied. In order to further improve IEEE Final Year
Project Domains practices we need to explicitly describe and utilise our knowledge about software domains of software engineering Final Year Project
Domains for CSE technologies. This paper suggests a modelling formalism for supporting systematic reuse of software engineering technologies
during planning of software projects and improvement programmes in Final Year Projects for CSE.
Software management seeks for decision support to identify technologies like JavaScript that meet best the goals and characteristics of a software
project or improvement programme. JavaScript Training in
Chennai Accessible experiences and repositories that effectively guide that technology selection are still lacking.
Aim of technology domain analysis is to describe the class of context situations (e.g., kinds of JavaScript software projects) in which a software
engineering technology JavaScript Training in Chennai can be applied successfully
The Angular Training covers a wide range of topics including Components, Angular Directives, Angular Services, Pipes, security fundamentals, Routing,
and Angular programmability. The new Angular TRaining will lay the foundation you need to specialise in Single Page Application developer. Angular Training
This is nice blog I have seen and read it you have defined all in short way. I am accountant and service provider and provide bas returns Thats why I don't know what's the topic but when I read it I know all the thing.
Merkur Super Light and Safety Razor - deccasino.com
Merkur Super Light and Safety Razor is designed for an ideal 제왕카지노 match 메리트 카지노 head for shaving, razors septcasino and other recreational wet shavers. The Merkur Super Light
buy the most trending louis replica handbag simply by clicking on the monogram lv neverfull
"The blog provides valuable insights into simulating and demonstrating various attack scenarios using Microsoft Advanced Threat Analytics (ATA). These simulations help users understand and test the capabilities of ATA in identifying and protecting against advanced targeted attacks, such as communication issues, honey token account activities, massive object deletion, and reconnaissance using DNS. It's an informative resource for understanding hrm thesis writing service ATA's functionality in a practical context."
Post a Comment