Original post - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html
The Microsoft Azure Multi-Factor Authentication (MFA) provides various authentication types when using an on-premises MFA server. The Company Settings section allows the Multi-Factor Authentication (MFA) administrator to define company wide settings for all users.
The administrators can also make (or override) individual user configuration from User Section.
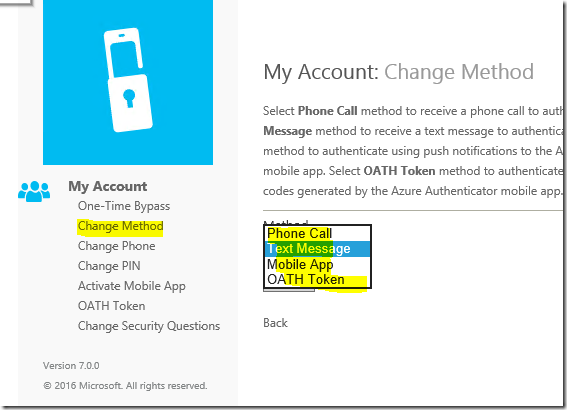
An end user can make their own sections from the the User Portal.
In general, the following authentication modes are available when using an on-premises MFA server. The purpose of this blog is to explain each of these authentication types and expected result with screenshots.
- Phone call (Standard)
- Phone call (PIN)
- Text message (One-way OTP)
- Text message (Two-way OTP)
- Text message (One-way OTP + PIN)
- Text message (Two-way OTP + PIN)
- Azure Authenticator application (Standard)
- Azure Authenticator application (PIN)
- Azure Authenticator application (OATH token)
- Third Party OATH token
In this blog, I will be covering the following authentication types.
- Azure Authenticator application (Standard)
- Azure Authenticator application (PIN)
- Azure Authenticator application (OATH token)
- Third Party OATH token
Review Part I of this blog for other authentication type details.
The Azure Mobile App mode results in a notification being sent to the user's Azure Authenticator mobile app. There are 2 different modes for Mobile App – Standard and PIN mode.
Azure Authenticator application -Standard
In this mode, user will be prompted for primary authentication using a user name and password and the second authentication is when the user receives a notification in the Azure Authenticator mobile app.
Expected Result
In Standard Mode, users will prompted to authenticate, deny, or deny and report fraud as shown below:
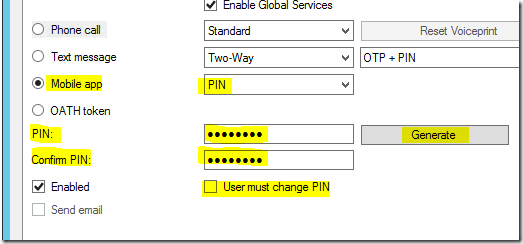
Azure Authenticator application – PIN
The PIN mode enhances the security of the Multi-Factor Authentication by requiring the user enter a PIN in the Azure Authenticator mobile app.
Expected Result
In this mode, user will be prompted for primary authentication using a user name and password and the second authentication is when the user receives a notification in the Azure Authenticator mobile app to enter the PIN number as shown below:
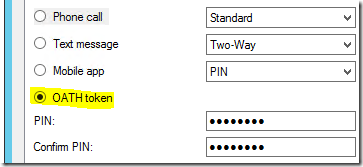
Azure Authenticator application - OATH token
Oath Token mode results in the user being prompted for an OATH code to authenticate with Multi-Factor Authentication. Time-based OATH codes can be generated by the Azure Authenticator Mobile App or a third-party token. We will start with Azure Authenticator Mobile App. As shown in the following screenshot, the OATH Tokens (Enable OATH Tokens) must be enabled in the MFA Server console to display a Time-based OATH codes in Azure Authenticator Mobile App. keep in mind that the OATH Token method is only supported by RADIUS Authentication and IIS Authentication Form-Based Authentication.
After the activation of Mobile App, users can select OATH token mode from the User Portal or an administrator can configure this from a MFA server console.
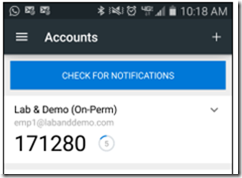
Expected Result
A Time-based OATH codes will be generated by Azure Authenticator Mobile App as shown below.
This code needs to entered in the respective application to complete the second factor authentication.
Third Party OATH token
Azure MFA server supports a time based OATH (OATH – TOTP) third party tokens. This is an alternative to using the Azure Authenticator mobile app as an OATH token (see the above scenario - Azure Authenticator application -Standard). OATH tokens can be added or imported prior to being associated with a user. Administrators can associate users and tokens in the Multi-Factor Authentication Server (as shown below) or the User Portal. Users can associate themselves with an OATH token during User Portal enrollment or using the OATH Token menu option when the User Portal is configured to provide this functionality. A bulk token import and configuration is also supported by MFA Server . An administrator can import OATH Token records from an input file . The secret keys must be in Base32 format.
For this scenario, I am using Yubikey 4 (Yukico) OATH token as the third party OATH token. You need to use Yubico Authentication application to get the OATH code from Yukikey. Review my Azure MFA and Yubico OATH configuration blog for the configuration details.
The OATH token option is same as the Azure Authenticator mobile app configuration as shown below:
Expected Result
In this scenario, you will be using the Time-based OATH codes generated by Yubico Authenticator application.
This OATH code must be entered in the respective application to complete the second factor authentication.
If you have Azure Mobile App OATH and a third party OATH token active for the same user, both token code will be valid.
























15 comments:
Great information shared in this blog. Helps in gaining concepts about new information and concepts. Awesome information provided. Very useful for the beginners.
CCNA Openings in Hyderabad .
Thanks for your post! Through your pen I found the problem up interesting!
Useful websites: download videos from everywhere instagram video downloader, read comics online for free in high quality and most full.
nice one good job
Great guide man! It’s easy to see that you know it so well. If only I could know it as you do. Because it’s always a pain in the butt, trying to understand what’s wrong with it. If I didn’t have people like you with their blogs about this kind of problems I tell you I would hang myself or at least I would change my job! The same thing with essay. If I didn’t have any services who could help me with some casual question like how to write a reflective essay for university. I think, I would be doomed as well.
Awesome, great guide! thanks for taking the time to write and share it!
You guys should also check out this tutorial, guys.
Great information shared in this blog. It’s very easy to see that you know it so well.
yahoo com mail
Regarding the article you wrote, I was really inspired once. But can you provide me with more relevant data? Because in your article I get few basic points though overall, your article is good enough.
link alternatif sbobet
Windows Azure officially supports DeepNet SafeID hardware tokens which are OATH compliant. You might want to check it out:
http://www.deepnetsecurity.com/authenticators/one-time-password/safeid/
http://wiki.deepnetsecurity.com/display/KB/How+to+Import+SafeID+Token+into+Azure+MFA+Server
I'm glad to find this article. Thank you!
imgrum
Such a nice post, I found a lot of interesting things in this blog. The information was nice and useful, helps me so much. Thanks for sharing this post.
pikbee
Main Permainan Judi Casino Online Login joker123 memang merupakan jenis taruhan yang paling seru untuk di mainkan, karena sudah memiliki jackpot besar, banyak juga jenis permainan yang disediakan.
Post a Comment