Related Blogs:
Configuring YubiKey / Yubico OATH Token with Microsoft Azure MFA Server - http://portal.sivarajan.com/2016/06/configuring-yubikey-yubico-oath-token.html
Azure MFA with pGina and Local Authentication - http://portal.sivarajan.com/2015/09/azure-mfa-with-pgina.html
Azure MFA Server –Authentication Types (Part I) - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
Azure MFA Server –Authentication Types (Part II) - http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html
Microsoft Azure MFA on-premises server supports a time based OATH (OATH – TOTP) third party tokens. This is an alternative to using the Azure Authenticator Mobile App as an OATH token. You can see other MFA authentication options in my Azure MFA Server–Authentication Types (Part I) and Azure MFA Server–Authentication Types (Part II) blogs. The OATH tokens can be added or imported prior to being associated with a user. Administrators can associate users and tokens in the Multi-Factor Authentication Server or the User Portal. Users can associate themselves with an OATH token during User Portal enrollment or using the OATH Token menu option when the User Portal is configured to provide this functionality. A bulk token import and configuration is also supported by MFA Server . An administrator can import OATH Token records from an input file . The secret keys must be in Base32 format.
This blog provides step-by-step instructions in configuring Deepnet SafeID OATH token with Microsoft Azure MFA server. I am using DeepNet Security's SafeID Classic model for this testing. You can review different token models and details on their website.
Requirements:
The following are the pre-requirements to complete this configuration.
- Microsoft Azure MFA on-premises server
- Deepnet SafeID hardware
- Secret Key for your DeepNet SafeID. You will receive an email with Secret Key after the purchase.
Review the following Azure MFA Server Authentication Types blog if you are not familiar with authentication configuration in Azure MFA Server:
Azure MFA Server –Authentication Types (Part I) - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
Azure MFA Server –Authentication Types (Part II) - http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html
Azure MFA Server – Configuration for third Party OATH
First step in this process is to add third party OATH Tokens in Azure MFA Server. You can either add these tokens individually or perform a bulk import using an input file.
To add an OATH token,
- Logon to your MFA application server. Open Multi-Factor Authentication Server UI and Select OATH Token icon.
- Click Add option from OATH Token window.
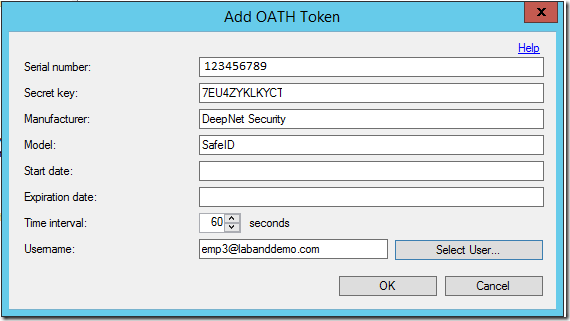
- Enter your Secret Key token Details
- Serial Number – Required. Enter the serial number of your SafeID. This will be in the back of the Secret Keyas shown below or it will be the email you received from DeepNet.
- Secret Key – Required. This is the Secret Key (Base32). You have to receive this information from DeepNet. You will receive an email from Deepnet with Secret Key after the purchase
- Manufacturer – Optional. Enter DeepNet Security as the manufacturer.
- Model – Optional. Enter SafeID as model type.
- Start date – Optional
- Expiration date – Optional
- Time interval – Required. Select 60 seconds.
- Username: Associate a user with this OATH token. You can manually enter the username or Select User option to identify a user.
- Click OK to complete. The Synchronize OATH Token dialog will prompt for the current OATH code to synchronize the OATH token and verify the configuration.
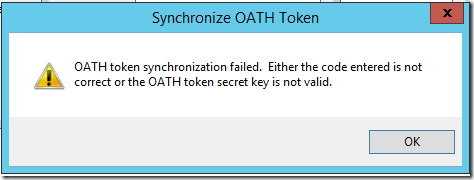
- Enter the current code from DeepNet SafeID from the Synchronize OATH Token window to complete token configuration in MFA Server. Click OK.
Note1: MFA server validates the OATH code against the OATH token secret key and synchronizes the OATH token's time if they are valid. If there are not valid, you will see the following error message:
Note2: Azure Multi-Factor Authentication Server supports bulk import of token records by using an input CSV file. The file must be in a supported format and may be partially or fully encrypted with a password.
To perform a bulk import,
Note3: you may receive the following error message when you click on Import button. There is an update/hotfix for this issue.
Unhandled exception has occurred in your application. If you click Continue, the application will ignore this error and attempt to continue. If you click Quit, the application will close immediately.
Could not load file or assembly ‘PfPskcClr, Version=0.0.0.0, Culture=neutral, PublicKey Token=null’ or one of its dependencies. A strongly-named assembly is required. (Exception from HRRESULT:0X8013100)
Azure MFA Server – End User Validation Using DeepNet SafeID OATH Token
The final step in this process is to validate the DeepNet SafeID configuration and authentication experience from an end user perspective.
To configure OATH token as the authentication type for an end user:
- From Multi-Factor Authentication Server UI, Select Users icon
- From right pane, open the user properties by double clicking the user object.
- This will open User Properties / Edit User window as shown below. Make sure that the OATH Token is selected as the authentication type for this test user.
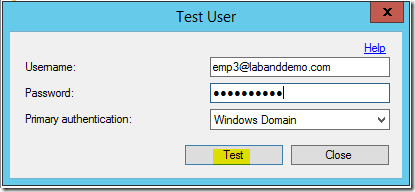
- To validate this configuration, select out test user object and from the bottom of the window, select Test option.
- User will be prompted for first /primary authentication using a user name and password. Enter the User name and Password for the user, then click Test.
- Then it will prompt you for the secondary authentication. In this scenario, it the OATH Code.
- Get the current OATH code from your DeepNet SafeID.
- Enter the current code in the OATH Code window in the MFA application . Click OK.
- You will see the authentication status/result as shown below:
Related Blogs:
Configuring YubiKey / Yubico OATH Token with Microsoft Azure MFA Server - http://portal.sivarajan.com/2016/06/configuring-yubikey-yubico-oath-token.html
Azure MFA with pGina and Local Authentication - http://portal.sivarajan.com/2015/09/azure-mfa-with-pgina.html
Azure MFA Server –Authentication Types (Part I) - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
Azure MFA Server –Authentication Types (Part II) - http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html

























16 comments:
This is exceptionally advantageous when you need to make a more definite investigation of this particular theme furthermore I might want to value all your exertion with the readers. Much appreciated. Like wise custom essay writing service is also a good source for the students to solve essay writing related doubts.
This is a brilliant stuff and you have explained each part in a good manner with the help of diagrams and screenshots. Admission essay writing service
You have explained the technical aspects in a good manner. This blog offers intense detailing of the topic. UK dissertation writing service
Safe ID is very important when it comes to security of anything www.smfollowersguru.com
http://cheatskit.com/ get the free games
wwe draft bst work
.This is a great article, that I really enjoyed reading. Thanks for sharing.
friv games
superfighters
that is one of the toughest security measures you can come across
Windows Azure officially supports DeepNet SafeID hardware tokens which are OATH compliant. You might want to check it out:
http://www.deepnetsecurity.com/authenticators/one-time-password/safeid/
http://wiki.deepnetsecurity.com/display/KB/How+to+Import+SafeID+Token+into+Azure+MFA+Server
IEEE Projects on Information Security
Great Article
IEEE Projects on Information Security
Project Centers in Chennai
JavaScript Training in Chennai
JavaScript Training in Chennai
I’m excited for soup season, too. In fact, I think I might just need to make this for dinner tonight happy wheels!
Hi There...Is there a possibility of OATH token time going out-of-sync. Codes we generate from a token doesn't work immediately. However, works when used after 5 minutes.
At Deepnet Security we have just put a web page for users of Azure and Office 365 who want to authenticate using SafeID oath tokens etc.
More details can be found from the following link;
http://www.deepnetsecurity.com/authenticators/one-time-password/safeid/hardware-mfa-tokens-office-365-azure-multi-factor-authentication/
Thank you for providing this interesting and very interesting topic. I will update your next post often.
xem truc tiep bong da hom nay and truc tiep bong da
If you need a current link with instructions on adding SafeID hardware tokens to azure MFA you can find instructions using the following link;
https://wiki.deepnetsecurity.com/pages/viewpage.action?pageId=3834772
The Azure cloud platform consists of more than 200 products and cloud services that are designed to help you develop innovative solutions and tackle today's issues. Build, execute, and manage applications with the tools and frameworks of your choosing across various clouds, on-premises, and at the edge. Azure training in chennai
Post a Comment