The current Azure MFA doesn't have a plug-in for local workstation and sever authentication. So I was testing some other scenarios using an open source application called pGina. You can read more information here - http://pgina.org/ .
PGina supports different protocols, for this testing I was using RADIUS . From an MFA perspective, it is same as any other RADIUS and 2FA configuration. Here are some of my notes:
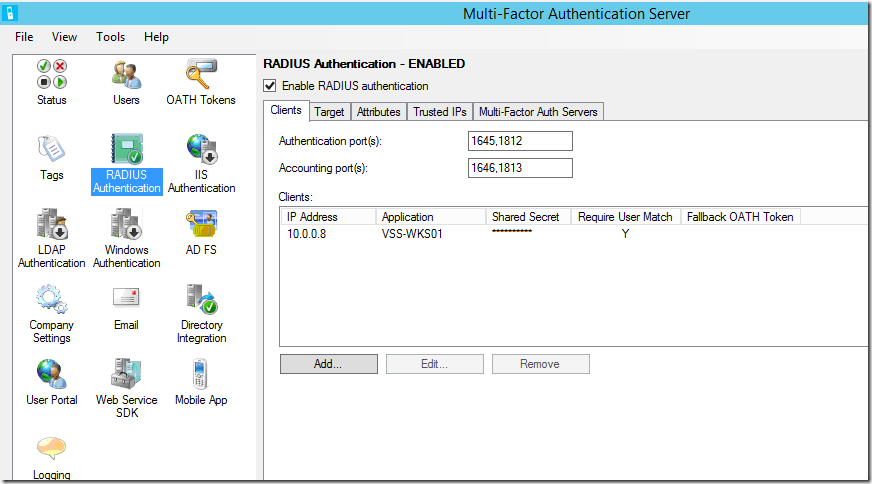
Azure MFA and RADIUS configuration details are well documented in https://azure.microsoft.com/en-us/documentation/articles/multi-factor-authentication-get-started-server-radius/ so I am not planning to add any details here. For this testing, I have added my client machines as “Clients” as shown in the following screenshot:
Since I am using domain joined machines, I have selected Windows Domain as the target.
Those are the only configuration you need to make on the MFA server. Next step is to configure the PGina application on your workstation – of course it has to be locally installed on the machine. Open pGina application from the workstation and select the appropriate plug-in. I have selected RADIUS.
Select Configure button to enter your MFA server information.
You don’t need to make any other changes unless you are planning to configure multiple authentication and priorities. From the Simulation tab, you can validate your authentication configuration. Based your MFA configuration (Phone call, Text message, Mobile app, OATH token) the user will receive a second after authentication prompt.
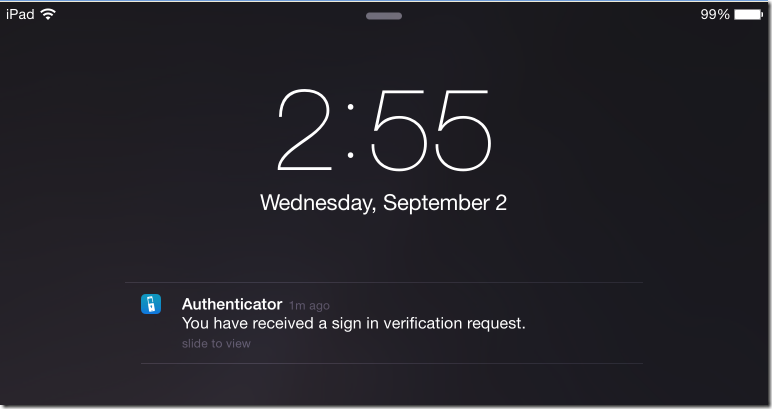
Since my test account was configured to use MFA Mobile App, I received the following 2FA request on my configured device.
You will also see the authentication status in the Result section.
If your MFA server is in Azure or planning to connect it remotely, make sure to open the appropriate ports. In Azure, additional End Points (port 1812 and 1813) need to be opened for your MFA.
Note: You are enabling public access to your servers. Understand the risk before making these configuration changes :)
You also need to modify pGina client with correct Azure server name or IP address. It is easier to use the Cloud Service name (name.cloudapp.net).




















6 comments:
Thank you so much for this wonderful blog..This website consists of informative posts only. Very helpful..
It will be great idea for students to check the info from https://essayclick.net/blog/responsibility-essay out. Especially if you need to write your essay about responsibility soon.
I truly grateful for this post. I’ve been trying everywhere for this! Impart goodness I found it on this post. I really esteem your work and that I expect in future I’ll come back for additional data. Like this one. Some points described here were new for me and it was really wonderful to go through such informative post. You have created my day! Thanks again!
web: Essay Writing Service
Thank u for such great and well written post. BTW u should check amazing explanation about physical beauty vs inner beauty
Hello! I know that nit every person has time for writing papers in the best way. That's why more and more people buy unique essay and save their time.
Hello, I would like to thank you for sharing this interesting information, the material you have provided here will be useful for my https://writessay.org task.
Post a Comment