Original post - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html
The Microsoft Azure Multi-Factor Authentication (MFA) provides various authentication types when using an on-premises MFA server. The Company Settings section allows the Multi-Factor Authentication (MFA) administrator to define company wide settings for all users.
The administrators can also make (or override) individual user configuration from User Section.
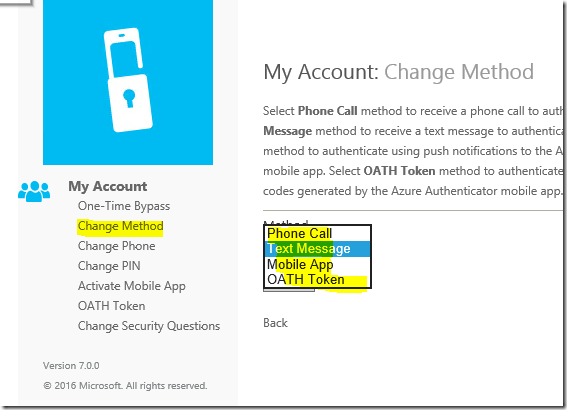
An end user can make their own sections from the the User Portal.
In general, the following authentication modes are available when using an on-premises MFA server. The purpose of this blog is to explain each of these authentication types and expected result with screenshots.
- Phone call (Standard)
- Phone call (PIN)
- Text message (One-way OTP)
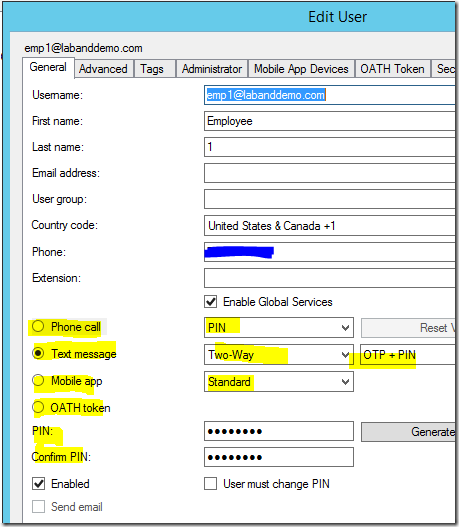
- Text message (Two-way OTP)
- Text message (One-way OTP + PIN)
- Text message (Two-way OTP + PIN)
- Azure Authenticator application (Standard)
- Azure Authenticator application (PIN)
- Azure Authenticator application (OATH token)
- Third Party OATH token
We will start with standard Phone Call option. The Phone call authentication type has two sub options:
- Phone call (Standard)
- Phone call (PIN)
Authentication Type : Phone Call – Standard
Expected Result
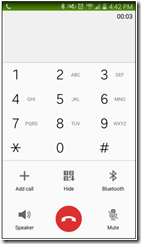
In this mode, user will be prompted for first authentication using a user name and password and then the second authentication is based on the phone call as shown below:
The first authentication is based on the configuration in MFA. For example, for RADIUS, you an select the following options from the Target tab:
The “from” telephone number can be customized from azure console (https://manage.windowsazure.com/ –> Active Directory –> Configure –>Multi-factor Authentication –> Manage Service Settings –> Go to the Portal –> Configure –> Settings –> General Settings –> Caller ID Phone Number) as shown below:
Also, the Voice Messages can be customized based on your requirements. This option is available in https://manage.windowsazure.com/ –> Active Directory –> Configure –>Multi-factor Authentication –> Manage Service Settings –> Go to the Portal –> Configure –> Voice Message section.
Authentication Type : Phone Call – PIN
In this scenario, we will use Phone call with PIN option.
Expected Result
In this mode, user will be prompted for first authentication using a user name and password and then the second authentication is based on the phone. During the phone call, MFA will ask you to enter a personalized PIN.
The PIN creation and enforcement is based on the following configuration in user section.
You also have an option in Company Settings section to enforce default PIN rules as shown below:

- Text message (One-way OTP)
- Text message (Two-way OTP)
- Text message (One-way OTP + PIN)
- Text message (Two-way OTP + PIN)
Authentication Type : Text message - One-way OTP
Expected Result
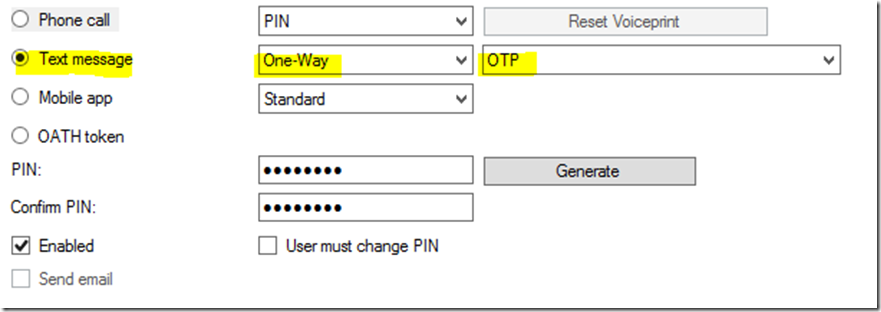
In this mode, user will be prompted for first authentication using a user name and password and then the second authentication is based on a text message containing a One-Time Passcode (OTP) is sent to the user as shown below:
The user must enter this One-Time Passcode (OTP) in the respective application to complete the authentication request. You application must support Challenge – Response (Authentication Chaining).
Authentication Type : Text message – Two-way OTP
Expected Result
In this mode, user will be prompted for first authentication using a user name and password and then the second authentication is based on a text message containing a One-Time Passcode (OTP). The user must reply to the same text message by entering the provided OTP to complete the authentication request as shown below:
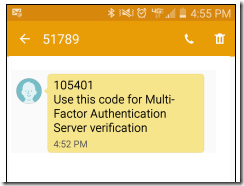
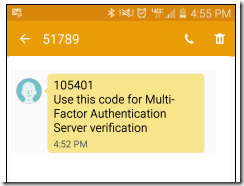
Authentication Type : Text message - One-way OTP + PIN
Expected Result
In this mode, user will be prompted for first authentication using a user name and password and then the second authentication is based on a text message containing a One-Time Passcode (OTP) is sent to the user as shown below:
This One-Time Passcode (OTP) + PIN needs to be entered in the application to complete the authentication request.
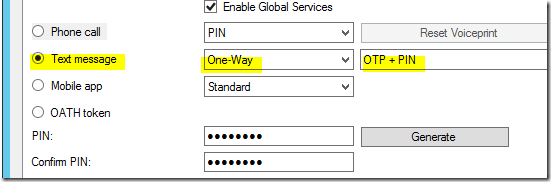
The PIN values is based on the configuration in the user or Company Settings:
User settings:
Company Settings:
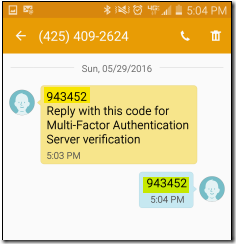
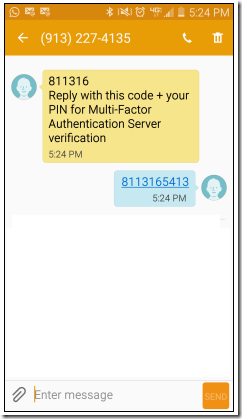
Authentication Type : Text message – Two-way OTP + PIN
Expected Result
In this mode, user will be prompted for first authentication using a user name and password and then the second authentication is based on a text message containing a One-Time Passcode (OTP) + PIN. The user must reply to the same text message by entering the provided OTP + their personal PIN to complete the authentication request as shown below:
I believe we have enough information and screenshots for this blog . I will cover the following authentication types in the Part-II of this blog:
- Azure Authenticator application (Standard)
- Azure Authenticator application (PIN)
- Azure Authenticator application (OATH token)
- Third Party OATH token




























14 comments:
I'm not certain the place you are getting your information, however great topic. I needs to spend a while learning more or working out more. Thank you for great info I was in search of this info for my mission. paypal login
What a detailed tutorial! Thank you very much!
pictaram
If you wanna know more information, click here, my friends.
Really it is very useful for us..... the information that you have shared is really useful for everyone. If someone wants to know about EHS Software and Health and Safety Software I think this is the right place for you.
https://www.acte.in/php-training-in-chennai
https://www.acte.in/machine-learning-training-in-chennai
https://www.acte.in/iot-training-in-chennai
https://www.acte.in/blockchain-training-in-chennai
https://www.acte.in/openstack-training-in-chennai
A reverse mortgage loan can sometimes require settlement costs which would make it impractical being a short-term solution in a few cases. articles
In addition to a really good rate, were also interested in providing great service, in a highly professional and trustworthy manner that earns clients' respect. canadian mortgage calculator Super responsive, great at explaining things (even whenever you don't know much about the way the mortgage world works) plus it's clear sherrrd like the absolute best to be with her clients. mortgage calculator
Our service https://freepaperwriter.com/ is trusted by students all over the world. We know what they need because we listen to them. That is why every essay you buy from us is 100% original to you.
Hello. Every business needs to keep clients base, manually - it is tough, but call-tracking software - is good solution. Here there is calltrackers reviews platform
Live casinos take your common game of roulette and make it much more immersive. After all, an 솔카지노 actual vendor will spin an actual wheel with a ball, and you’ll be able to|be capable of|have the flexibility to} hear the identical acquainted sound of the wheel as you'll at a land-based casino. Asia is the place where Macau, Singapore, and the Philippines are situated and every passionate participant is dreaming of rolling the dice in one of many exclusive casino resorts there.
Implementing Azure MFA Server is a significant step in enhancing security, especially when dealing with sensitive data. However, it’s crucial to remember that even with advanced tools, cyber threats remain a real concern. I recently read about Baazov, a cybercriminal who exploited digital systems to commit fraud. His actions are a stark reminder that no system is completely immune to attacks. As someone invested in cyber security, I believe that while tools like Azure MFA are vital, constant vigilance and regular updates are equally important. Protecting our systems from threats like Baazov ensures the safety and integrity of our digital environments.
Drive Mad has quickly built a loyal community of players. Online forums, social media groups, and YouTube channels dedicated to the game are filled with tips, tricks, and fan-made content.
flappy bird had become viral for several reasons: simplicity, retro aesthetic, challenging gameplay, etc. Try it then!
Golf Orbit is a golf game with no time or level limits, creating a continuous race between players to achieve the highest score and challenge friends.
Post a Comment