Microsoft Advanced Threat Analytics (ATA) is an user and entity behavior analytics solution to identify and protect protect organizations from advanced targeted attacks (APTs). You can read more information about Microsoft Advanced Threat Analytics (ATA) here. The purpose of this blog is to provide a few methods which can be used to simulate and demonstrate some of the basic attacks for demo and testing purpose.
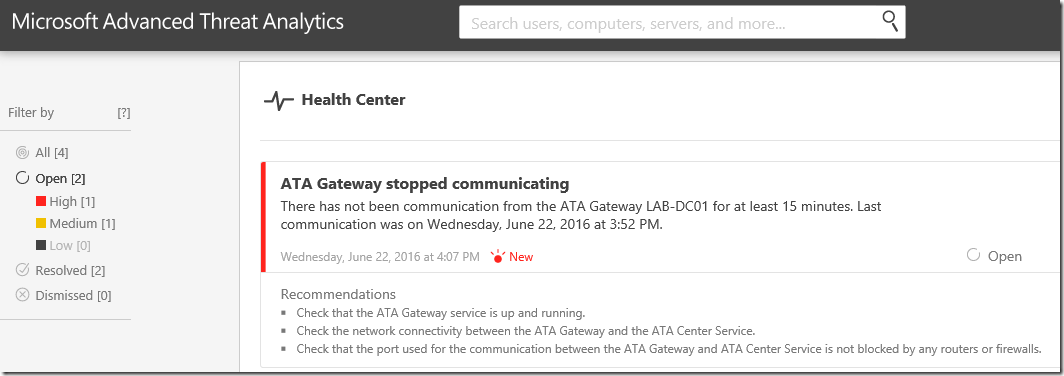
Suspicious Activity Simulation #1 – ATA Gateway Stopped Communicating
We will start with the most obvious one! – ATA communication issue. In this scenario, I am using ATA Light Weight Gateway(LWGW). In this case Microsoft Advanced Threat Analytics Gateway (ATAGateway) service should be running on Domain Controllers.
To simulate this scenario,
- Identify all Domain Controllers from the forest/domain. You can use the following DSQUERY command to get all DCs from the domain.
- DsQuery Server -Forest
- DsQuery Server -Forest
- Stop the ATAGateway service remotely
Suspicious Activity Simulation #2- Honey Token Account Activities
In general, the Honey Token accounts are non-interactive accounts. These accounts can be dummy accounts for detect malicious activities.
To simulate this scenario,
- Create two 2 user accounts in Active Directory (ATA-Test1 and ATA-Test2)
- Add ATA-Test2 to Domain Admins group
- Get the SID of ATA-Test1 and ATA-Test2 using PowerShell or DSQUERY command
- Add this SID as Honey token accounts (ATA Console –> Configuration –> Detection –> Honeytoken Account SIDs). Save the configuration.
- Establish an integrative logon session using these accounts. You can RDP into a machine use these accounts
You will receive the following alert/email with recommended actions in the ATA console.
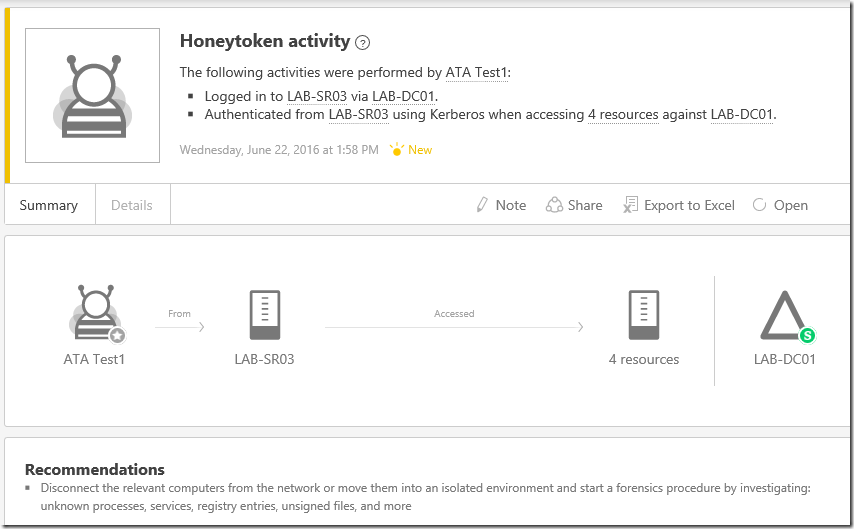
Honey Token accounts (Sensitive)
Since ATA-Test2 account is a domain admin account, you will receive the same alert with "Sensitive (S )" indicating that this account is a high privileged account in Active Directory.

Suspicious Activity Simulation #3 – Massive Object Deletion
Bulk object deletion can be a suspicious activity in an Active Directory environment. ATA can alert alert you based on massive object deletion activities.
To simulate this scenario,
- Create a few users in Active directory. Here is a sample PowerShell script which you can use to create test accounts in Active Directory
ClearYou will receive the Massive Object Deletion alert in the ATA console right away as shown below.
Import-module activedirectory
$pass = ConvertTo-SecureString "MyPassword0!" –asplaintext –force
for ($i=0;$i -lt 100;$i++)
{
$accountname = "Test-Account$i"
Write-Host "Creating $accountname" -NoNewline
New-ADUser –SamAccountName $accountname –name $accountname -OtherAttributes @{'description'="ATA Test User Account"} -Path "OU=Test Accounts,OU=User Accounts,DC=labanddemo,DC=com"
Set-ADAccountPassword –identity $accountname –NewPassword $pass
Write-Host "...Done"
}

Suspicious Activity Simulation #4 - Reconnaissance using DNS
The DNS or name resolution information in a network would be useful reconnaissance information. In general, DNS data contains a list of all the servers and workstations and the mapping to their IP addresses. Verifying this information may provide attackers with a detailed view of the environment allowing attackers to focus their efforts on the relevant entities.
For this simulation, the plan is to perform a DNS zone lookup using NSLOOKUP LS command.
To simulate this scenario,
- Logon to a remote server.
- Open Command Prompt and run NSLOOKUP command
- From the NSLOOKUP window, run LS command to list the DNS zone
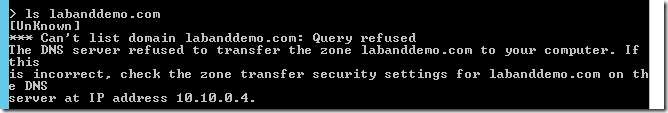
You will receive the following Reconnaissance using DNS alert the ATA console.

















17 comments:
Explore more articles on this topic at this website my friends.
This was a great way for me. pubg cheats
pubg hackpubg hack
pubg hacks
hacks for pubg
Thank you so much, this is very helpful for me.
instagram search
This is advanced software that can help organizations in getting protection from dangerous threats. Like the way write my uni assignment online uk based services are saving me from flunking from many semesters. So, we all must get the best protection available for protecting ourselves from cyber-attacks.
I have learned C++ sharp when I was in school and have learned C++11 at the University. Now I am doing a job as a Software Engineer in the reputed company which offers The best 6 person tent under $200 as a reward to the employee whose performance is the best throughout the month. The skills which I learned at the University are prooving very beneficial to me and I rewarded 2 times during 6 months of my job.
Excellent writing. I was just surfing and looking for a guide on PortOBlend why I found this wonderful article.
Excellent post, I am very happy after reading this post. Thanks. Keep sharing such stuff in future. Also try using Nulls Clash latest.
Analytics Gateway service should be running on Domain Controllers. communication issue. According to a survey, about 78 per cent of students in the United Kingdom are doing side jobs in order to manage their daily living expenses and tuition fee.
Dissertation Writing Services
These types of advanced software can eventually provide security and protect the organization from target attacks. I am working as an academic writer and providing all kinds of
Dissertation Writing Services UK
to students in crisis. I love to read such articles, which can enhance my knowledge about such safety software.
This is a great tool for keeping track of potential threats to your system. The Event Summary Reportprovides a clear and concise view of all the activity on your network, so you can quickly identify and respond to any threats.
Thank you for helping with this great information!
Regards: Lakeview Hotel Washington
The author's research and analysis provide a deep understanding of this topic. It is so appreciated!
Regards,
https://bakershomecleaning.com - The Best Cleaning Services In Atlanta GA
Nowadays, a hair fall problem can be seen in almost every human being. Whether someone is young or old, this issue is prevailing irrespective of any gender. There are multiple reasons that give rise to this particular problem, which is why everyone thinks to have an elizavecca cer 100 milky piggy hair treatment , to deal with it.
People are increasingly drawn to the idea of owning unique, digital assets, and one way to express their interest is by engaging in discussions and conversations on the largest nft marketplace
.
Ecommerce website developers understand the critical need for a secure online environment. ITG, your partner in building robust online stores, goes beyond website creation to guarantee your business is protected.
Great insights on emerging threats! It's crucial for organizations to stay proactive with their cybersecurity measures.<a href=https://fairfaxcriminallawyerva.com/fairfax-domestic-violence-lawyer/
The digital landscape is constantly evolving. I'm exploring options for online branding agency in karachi. Any recommendations for agencies that specialize in social media marketing and SEO for e-commerce businesses?
Post a Comment