Related blogs:
Configuring Deepnet Security SafeID OATH Token with Microsoft Azure MFA Server - http://portal.sivarajan.com/2016/07/configuring-deepnet-security-safeid.html
Azure MFA with pGina and Local Authentication - http://portal.sivarajan.com/2015/09/azure-mfa-with-pgina.html
Azure MFA Server –Authentication Types (Part I) - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
Azure MFA Server –Authentication Types (Part II) - http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html
Microsoft Azure MFA on-premises server supports a time based OATH (OATH – TOTP) third party tokens. This is an alternative to using the Azure Authenticator Mobile App as an OATH token. You can see other MFA authentication options in my Azure MFA Server–Authentication Types (Part I) and Azure MFA Server–Authentication Types (Part II) blogs. The OATH tokens can be added or imported prior to being associated with a user. Administrators can associate users and tokens in the Multi-Factor Authentication Server or the User Portal. Users can associate themselves with an OATH token during User Portal enrollment or using the OATH Token menu option when the User Portal is configured to provide this functionality. A bulk token import and configuration is also supported by MFA Server . An administrator can import OATH Token records from an input file . The secret keys must be in Base32 format. This blog provides step-by-step instructions in configuring YubiKey OATH token with Microsoft Azure MFA server.
Requirements:
The following are the pre-requirements to complete this configuration.
- Microsoft Azure MFA on-premises server
- YubiKey hardware
- YubiKey Personalization Tool
- YubiCo Authenticator Application
YubiKey Personalization Tool – Installation and Configuration
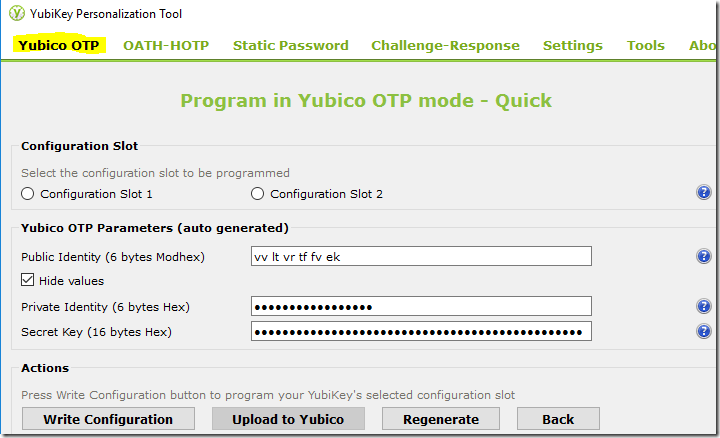
Microsoft Azure MFA server supports only the OATH TOTP (time-based) tokens. So you need to make sure that your YubiKey is in Yubico OTP Mode using the YubiKey Personalization Tool. Other configurations are optional for Microsoft Azure MFA server configuration and testing.
The YubiKey Personalization Tool can be used to program the two configuration slots. Also, it can be used to personalize the YubiKey in the following modes:
- Yubico OTP
- OATH-HOTP
- Static Password
- Challenge-Response
Download YubiKey Personalization Tool and run yubikey-personalization-gui-3.1.24.exe file to compete the tool installation.
- Insert YubiKey into the USB port. You may see the Device Setup windows as shown below. Complete the drive installation process.
- Open YubiKey Personalization Tool. Make sure:
- You will see all the current OTP configuration in Yubico OTP tab shown below. I am going to a use the default configuration for this testing.
YubiCo Authenticator Application – Installation and Configuration
Download YubiCo Authenticator Application and run yubioath-desktop-3.0.1-win.exe file to complete the application installation.
- Open YubiCo Authenticator Application
- From File menu, select Add option (File –> Add)
- From the New Credential window:
- Enter Credential Name – An identifier or a display name for the credential.
- Secret Key – It is a Base32 key. Review this If you are not familiar with supported numbers or characters in Base32 encoding.
- Select Time based (TOTP) option. Microsoft Azure MFA server supports only the OATH TOTP (time-based) tokens.
- Number of digits – You can select 6 or 8 digits as OATH token length.
- Require touch - If you select this option, end user has to touch the YubiKey to generate an OATH token. User will prompted with the following message:
- Click OK to save the configuration
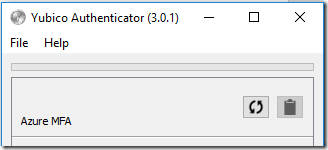
- You will see the newly add account in the Yubico Authenticator window.
Now we have completed the YubiKey account configuration. We can move on to Azure MFA server to configure the OATH token.
Azure MFA Server - Configuration for third Party OATH
Review the following Azure MFA Server Authentication Types blog if you are not familiar with authentication configuration in Azure MFA Server:
Azure MFA Server –Authentication Types (Part I) - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
Azure MFA Server –Authentication Types (Part II) - http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html
To add OATH Token in Azure MFA Server,
- Open Multi-Factor Authentication Server UI and Select OATH Token icon.
- Click Add option from OATH Token window.
- Enter your YubiKey token Details
- Serial Number – Required. Enter the YubiKey serial number. This will be in the back of the Yubikey as shown below:
- Secret Key – Required. This is the Secret Key (Base32) you have configured using the Authentication Application.
- Manufacturer – Optional. Enter Youbico as the manufacturer.
- Model – Optional. Enter your YubiKey model type.
- Start date – Optional
- Expiration date – Optional
- Time interval – Required. You can select the default 30 seconds value. By default, YubiKey changes the 6-8 digit code every 30 seconds.
- Username: Select the user for this OATH token. You manually enter the username or Select User option to identify a user.
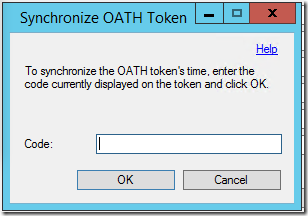
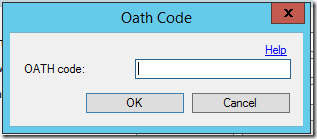
- Click OK to complete. The Synchronize OATH Token dialog will prompt for the current OATH code to synchronize the OATH token and verify the configuration.
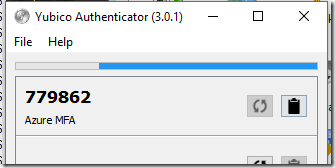
- Generate a new OATH from Yubico Authentication app using the
button.
- Enter this code in the Synchronize OATH Token window to complete token configuration in MFA Server.
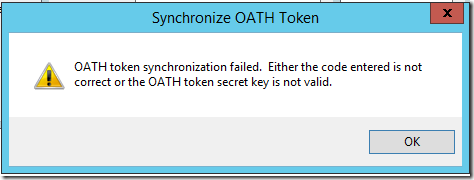
Note1: MFA server validates the OATH code against the OATH token secret key and synchronizes the OATH token's time if they are valid. If there are not valid, you will see the following error message:
Note2: Azure Multi-Factor Authentication Server supports bulk import of token records by using an input CSV file. The file must be in a supported format and may be partially or fully encrypted with a password.
To perform a bulk import,
- Select OATH Token icon and select Import.
- Select the input file and click Import.
Note3: you may receive the following error message when you click on Import button. There is an update/hotfix for this issue.
Unhandled exception has occurred in your application. If you click Continue, the application will ignore this error and attempt to continue. If you click Quit, the application will close immediately.
Could not load file or assembly ‘PfPskcClr, Version=0.0.0.0, Culture=neutral, PublicKey Token=null’ or one of its dependencies. A strongly-named assembly is required. (Exception from HRRESULT:0X8013100)
Azure MFA Server – End User Validation Using YubiKey OATH Token
The final step in this process is to validate the YubiKey configuration and authentication experience from an end user perspective.
To configure OATH token as the authentication type for an end user:
- From Multi-Factor Authentication Server UI, Select Users icon
- From right pane, open the user properties by double clicking the user object.
- This will open User Properties / Edit User window as shown below. Make sure that the OATH Token is selected as the authentication type for this test user.
- To validate this configuration, select out test user object and from the bottom of the window, select Test option.
- User will be prompted for first /primary authentication using a user name and password. Enter the User name and Password for the user, then click Test.
- Then it will prompt you for the secondary authentication. In this scenario, it the OATH Code.
- To generate a new OATH code, open Yubico Authenticator App and pressing the
 button . The OATH code will be displayed as shown below:
button . The OATH code will be displayed as shown below: - Enter the current OATH code in the OATH Code in the MFA application window. Click OK.
- You will see the authentication status/result as shown below:
Related blogs:
Configuring Deepnet Security SafeID OATH Token with Microsoft Azure MFA Server - http://portal.sivarajan.com/2016/07/configuring-deepnet-security-safeid.html
Azure MFA with pGina and Local Authentication - http://portal.sivarajan.com/2015/09/azure-mfa-with-pgina.html
Azure MFA Server –Authentication Types (Part I) - http://portal.sivarajan.com/2016/05/azure-mfa-serverauthentication-type.html
Azure MFA Server –Authentication Types (Part II) - http://portal.sivarajan.com/2016/06/azure-mfa-server-authentication-type.html


















![image_thumb[19] image_thumb[19]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEglCpp8Hu2n7WQ52r-4X1L3J_ul-Pqi8X0XYbzUbProRCgUMawAYczh4goqqLzPtAtvKwUjjRUd5J4L5FAIbfmNI7k1QDhezC-lBF4jgKLtccUtM0NlSiaom5vTnChO5lwfw-QJIAWtjRI/?imgmax=800)
![image_thumb[21] image_thumb[21]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj0cv6FLw2WsUNjLusJySN0sWNdNKuhPJ-DQzo0nRUZRicFYwj2W51aD9-XzY9Qt67xCPJfA9_SO-MJBc_H_ex9I9I1j_nTPX3Tm4hpFu1vKbKhNHieJTnOhmIphUSrkX4halSeITjMLUE/?imgmax=800)









14 comments:
Windows Azure officially supports DeepNet SafeID hardware tokens which are OATH compliant. You might want to check it out:
http://www.deepnetsecurity.com/authenticators/one-time-password/safeid/
http://wiki.deepnetsecurity.com/display/KB/How+to+Import+SafeID+Token+into+Azure+MFA+Server
Contactless tokens are more secure and reliable solution.
Protectimus offers tokens that are supported by Azure MFA:
Protectimus Two
https://www.protectimus.com/protectimus-two
Protectimus Slim mini
https://www.protectimus.com/slim-mini/
Deepnet Security has now created a new web page dedicated to hardware tokens for Azure MFA and Office 365, and provides information of how to use SafeID tokens with Azure MFA (see following link);
http://www.deepnetsecurity.com/authenticators/one-time-password/safeid/hardware-mfa-tokens-office-365-azure-multi-factor-authentication/
I hope the YubiKey installation process isn’t a whole extra load on my desktop. Luckily, I don’t have many important files right now, as I had a couple of months ago. Like, that time when a business student like me went for the best marketing essay writer there is, offering solutions on my long task piece topics and helping me ace through exams. So, I wouldn’t really mind even if my PC gets harmed now, LOL.
I have no idea, on how to use Microsoft Azure, neither do I care, because I need someone to help me get assistance to do health and social care level 2 assignments because my lack of understanding is not up to the task
Although I am not an IT guy still this information is as helpful for me as the best coursework help UK based. Because my boss is looking for a permanent server solution because employees are facing some accessibility issues. This will help in improving my image in front of the boss and maybe I can get a better appraisal.
My sister learned to use the alternative way of the Azure Authenticator Mobile App in her 10 lecture of her Google Analytics Class. She told me how were the students amused and delighted when they learned they were used MFA Server as an oath token easily.
There is some detail and an audio clip that you can listen to and get to know about KunstlerCast 275 — Art Berman Clarifies Whatever Happened to Peak Oil in case you are looking for the topic. You can also click to explore and learn about the things that can be heard here. That is something there are many who need to look forward to at this time of the year as well. You will find other sufficient data for same reason.
I know how to configure it. I have configured it in the past when I used to work at the best live security camera surveillance
NetEnt is dedicated to gaming that is enjoyable, protected, and secure. The most vital thing listed here are|listed beneath are} new applied sciences and that new video games shall be added to the portfolio quickly after their release. Inspired by the culture of the 카지노 Orient, Macao Roulette is featured with just one camera that is specifically positioned to constantly consideration to} the wheel and vendor. The iconic slot from Pragmatic Play is coming to Live Casino with all its wonderful and colourful options providing pleasure, volatility and mega multipliers in a Game Show format. Load up on sugar in Sweet Bonanza™, the 6×5, pays anywhere, tumbling videoslot. WIN A 2022 Jeep Grand Cherokee Limited Drawing Sunday, January 1, 2023 Earn Entries October 1- January 1, 2023 Gear up for a win!
Hello. If you want to find experienced professional MS developers, then do not waste your time! I found a site about developers who create the perfect program that will help you make your business easier and cover all your worries for a long time. You can find more helpful hints
Microsoft Azure is an incredible cloud computing platform that offers a wide range of powerful tools and services. Its scalability and versatility make it a valuable asset for businesses and researchers alike. By the way, if you're a Ph.D. student in need of technical assistance or research support, don't forget to explore phd dissertation assistance services. They can provide expert guidance on utilizing platforms like Microsoft Azure to optimize your research workflows and enhance the quality of your dissertation
Wow! I’ve always thought this topic was far too complicated for me to fully understand, but this writer made it so easy to follow. The way they broke everything down step by step was incredibly helpful. Kudos for making this information so much more accessible and understandable for all! Visit our link for ISO Certification in Saudi Arabia
Post a Comment